Integrating User Data with AD/LDAP
Integrating User Data with AD/LDAP
Because Enfold Server (ES) has hooks for Active Directory and Lightweight Directory Access Protocol (LDAP), this provides access to user data and login.
Giving Plone access to this information brings several benefits:
- Authentication. Enfold Server can use this user information to do authentication. (See Using AD for single sign on and Using LDAP for cookie-based login). By default, Enfold Server caches Active Directory queries every 10 minutes (although this can be changed).
- Mapping Groups to Plone Roles. You can create separate groups for each Plone role and then assign individual users to one or more groups as needed. (See Assigning Plone Roles to Active Directory Groups)
- importing user data for use by the content management system. When you choose an authentication profile in Enfold Server, that will make available tools for accessing user data from these directory services. After they are properly mapped, they can be called by or displayed within Plone.
This topic describes the data mappings between attributes of user records between LDAP/AD and Plone. You can use these data mappings to display user properties on the Plone site. For example, they could be displayed on a user profile page or on a department directory.
Filtering users in Active Directory
By default, when Plone fetches user or group objects from Active Directory (or LDAP), the query will return extra groups and users. For example, a query to list groups will probably pull out all security groups and computer names instead of actual users. You will probably need to narrow this query.
Active Directory lets you add filters (or subtrees) to improve server performance. One best practice involves creating an Organizational Unit (OU) called "Plone" and using this Organizational Unit as a filter for all your Active Directory queries.
If this Plone OU exists as a part of your Windows domain, that allows Plone to look up users from a restricted subset of users rather than having to query the entire set of users. When Active Directory contains a large numbers of users, this can improve login time and also reduce load on the Active Directory server.
If your Plone OU exists outside your Windows domain (i.e., if it contains both members of your Windows domain and nonmembers), you can add users to this Organizational Unit without having to grant them full access to the Windows domain. This can be useful when managing users who for one reason or another shouldn't have Windows domain accounts.
Configuring a AD filter within the Zope Management Interface (ZMI) is not hard; the only tricky part is remembering that you need to put the Plone filter at the beginning of the string value.
Note: the following applies to Active Directory, but the altering of LDAP queries is relevant to LDAP users too.
To add a filter, follow these steps:
- Site Setup > Authentication Profiles
- under your profile, click on Configuration or Group Configuration
In this screen you'll see two records, User Base DN and Group Base DN. These two fields are the LDAP queries that will be run against your Active Directory by default. By altering these queries you can alter what records are returned. As an example, suppose we wanted to limit the users available in Plone to only certain users in Active Directory. Here are some steps to do this:
using Active Directory management tools in Windows make a new organizational unit called Plone Users
add in the users you'd like to access from Plone into this organizational unit
in Plone add the organizational unit to the User Base DN query, adding in the text: OU=Plone Users, then click Update. Important: This text will look like this:
OU=Plone Users, DC=qehouston, DC=local
You can repeat similar steps for groups if you are pulling groups from Active Directory.
How Plone Maps User and Group Properties from AD and LDAP
Plone has user properties roughly similar to those used in AD and LDAP. They correspond to the Map to Name column in the tables below. Here are the default user properties for AD users. They are viewable in the Windows ADSI Directory.
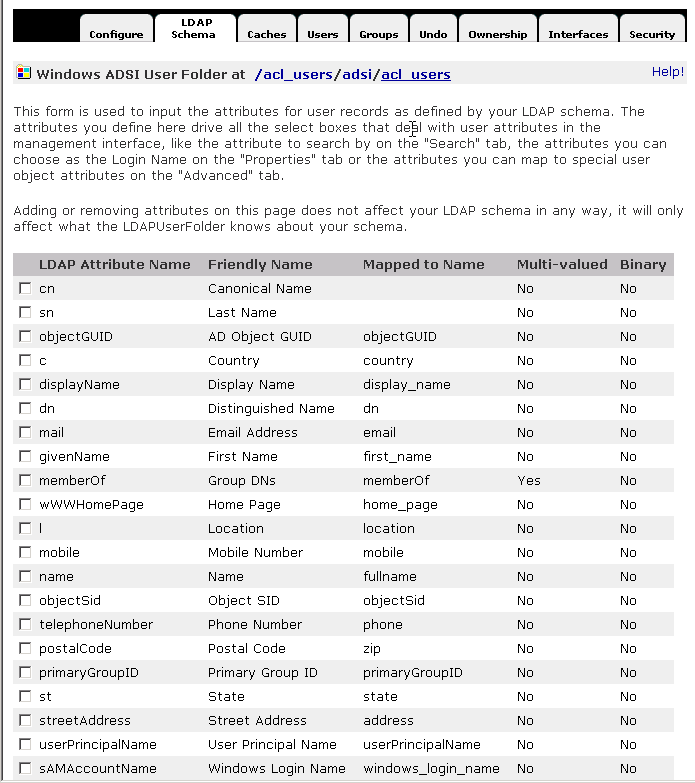
Here are the default user properties for LDAP users. They are viewable in the LDAPUserFolder.
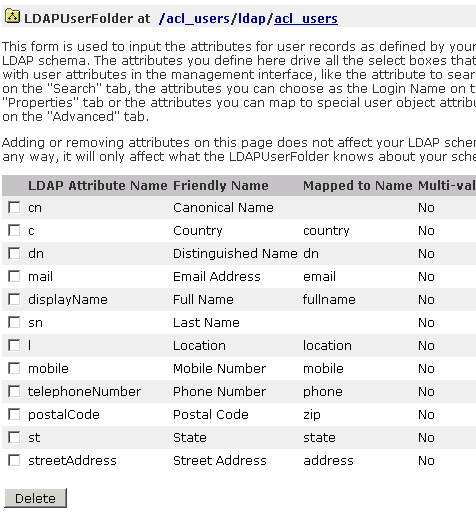
Once you know the Plone value for an AD/LDAP field, you can refer to them within Plone. If your directory service has different mappings for these values, then you can alter the settings by going to:
- Site Setup > Authentication Profiles > (Choose your authentication profile)
- click on Configuration or Group Configuration.